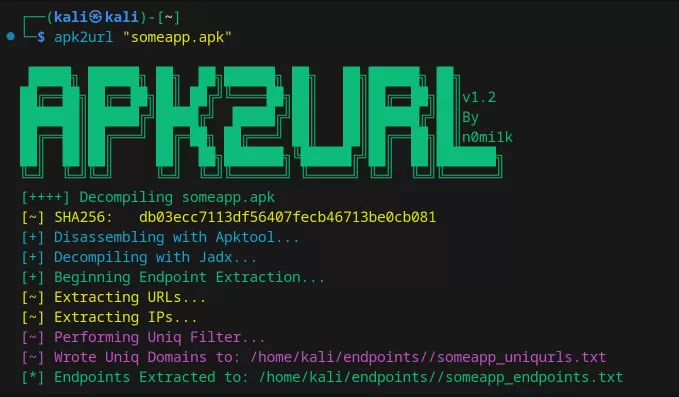
How to Extract Hidden Endpoints from APKs with apk2url
🔍 Extract Hidden Endpoints from APKs with apk2url
If you're into Android app analysis—whether as a pentester, red teamer, or developer—you know how important it is to discover all the hidden URLs, IPs, and API endpoints tucked away in APK files. Enter apk2url: a lightweight, powerful tool designed to uncover these with impressive accuracy and speed.
⚡ Why Choose apk2url?
There are plenty of APK analysis tools out there—like MobSF, APKLeaks, and AppInfoScanner. But apk2url stands out by uncovering a significantly higher number of endpoints, including deeply nested subdomains and log sources within the APK. It's fast, supports batch APK scanning, and has an easy setup process.
🛠️ Key Features
- Subdomain Enumeration – Detect unique domains and subdomains.
- URL & Path Extraction – Finds full URLs with GET parameters and paths.
- IP Address Finder – Automatically discovers embedded IPs.
- Log Sources – Optionally logs which APK files contain each endpoint.
- Multi-APK Scanning – Input a directory to scan multiple APKs at once.
- Simple Output – Generates clear `.txt` files with all findings.
📦 Installation Steps
apk2url depends on apktool and jadx, both easily available on Debian-based systems. Here’s how to set it up:
sudo apt update
sudo apt install apktool jadx
git clone https://github.com/n0mi1k/apk2url
cd apk2url
chmod +x install.sh apk2url.sh
./install.sh # Optional, makes apk2url available system-wide
🚀 How to Use apk2url
Once installed, scanning a single APK is as simple as running:
apk2url /path/to/app.apkWant to scan a whole folder of APKs in one go? Just point it to the directory:
apk2url /path/to/apk-directory/To enable logging of which files contain each endpoint, use the log option:
apk2url /path/to/app.apk log📂 Output Files Explained
By default, you’ll get results in the endpoints/ directory:
yourapp_endpoints.txt– Full URLs, URIs, and IPs found in the APK.yourapp_uniq.txt– A clean list of unique domains and IP addresses.
🧪 Best Practices for Usage
- Use on apps you own or have permission to test.
- Combine apk2url with other tools like MobSF for more comprehensive analysis.
- Always read endpoint logs to locate files responsible for network calls.
💡 Real-World Use Cases
- 📱 Extract API endpoints from competitor Android apps.
- 🔍 Find hardcoded IPs and test them for vulnerabilities.
- 👨💻 Check what your own app is exposing before a security audit.
📚 Resources
⚠️ Disclaimer
This tool is for educational and authorized testing purposes only. Never use it to analyze APKs you don't own or have explicit permission to test. The creators and contributors are not responsible for misuse.
Ready to dig deep into any APK? Give apk2url a spin and uncover what’s really under the hood! 🔍📱




Comments (2)
Leave a Comment